Using MCP With Cursor to Automate Incident Resolution
We announced in our previous blog that we are “meeting the developers in their backyard” with the launch of the Hawkeye MCP Server. In this blog, I want to show you a step-by-step demo of how to connect Hawkeye with Cursor IDE to dramatically improve the experience of responding to production issues.
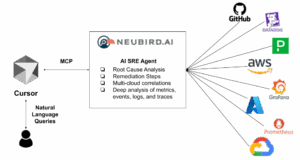
Hawkeye is our AI SRE Agent that connects to endpoints using read-only API calls. This includes AWS, Azure, Grafana, GitHub, Datadog, and more. The agent autonomously investigates any alerts and incidents, then conducts a deep analysis of the connected metrics, events, logs, and traces. The result is accurate Root Cause Analysis (RCA) and remediation steps.
The agent is available to access using MCP, and it gives engineers a single point of entry for reasoning with deep contextual insights from the entire infrastructure and application stack. Let’s take a look at how this works in practice using Cursor.
Connect Hawkeye with Cursor
Feel free to follow along with my steps by getting a free trial of Hawkeye here: https://signup.registration.neubird.ai/.
Once Hawkeye is configured, take note of your username, password, and URL. Then, set them as environment variables in a terminal, replacing the respective strings with your own.
export HAWKEYE_EMAIL=”your-email” export HAWKEYE_PASSWORD=”your-pw” export HAWKEYE_BASE_URL=”https://<env>.app.neubird.ai/api”
Launch Cursor from the same terminal so that it can inherit the variables. I will be showing the Cursor IDE example by running the ‘code’ command.
code
Note: If Cursor was open previously, you must fully exit the application and relaunch it from the command line to inherit the environment variables.
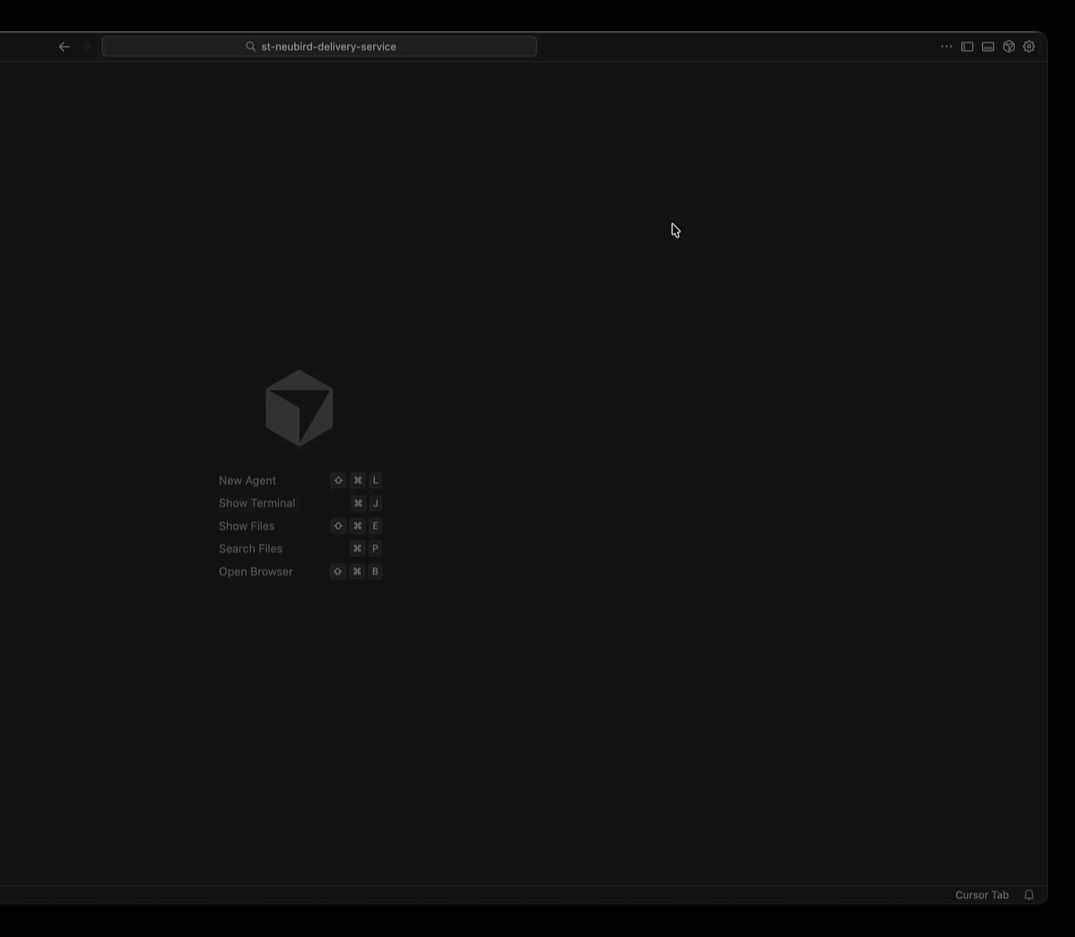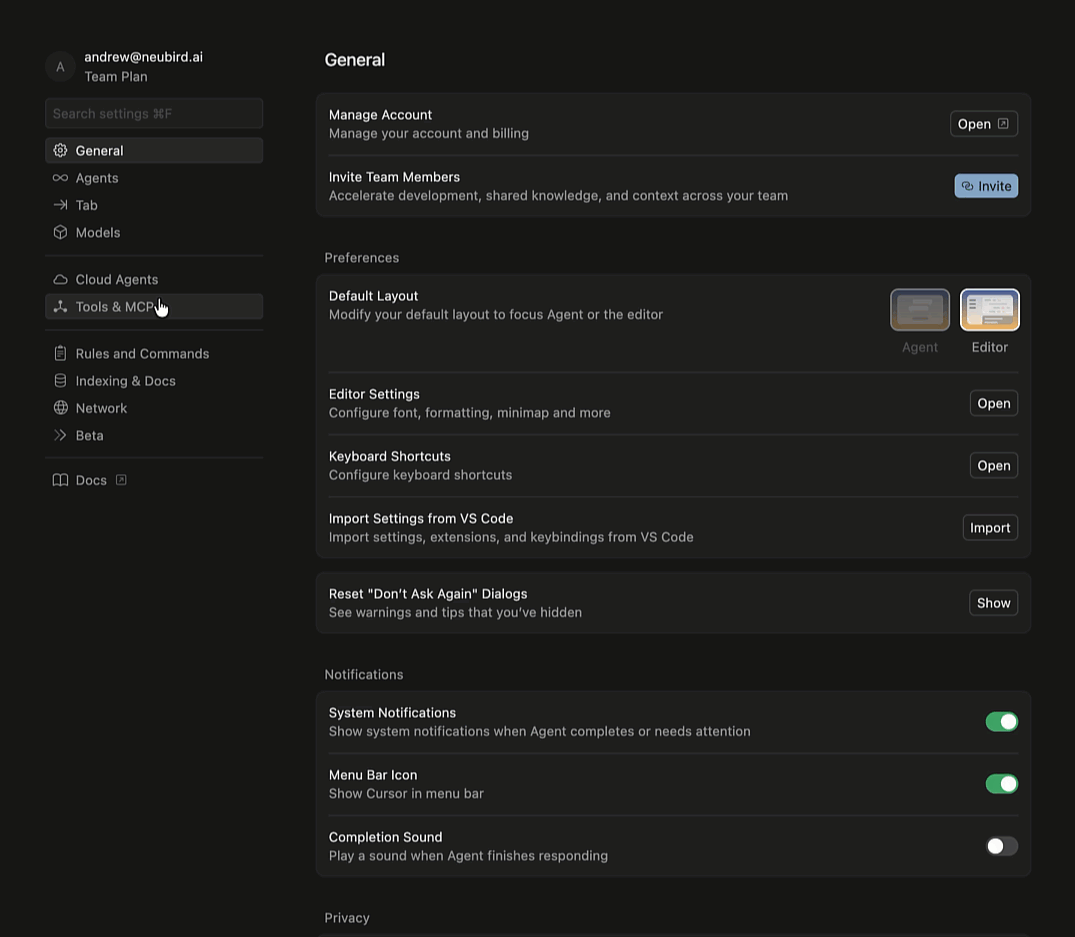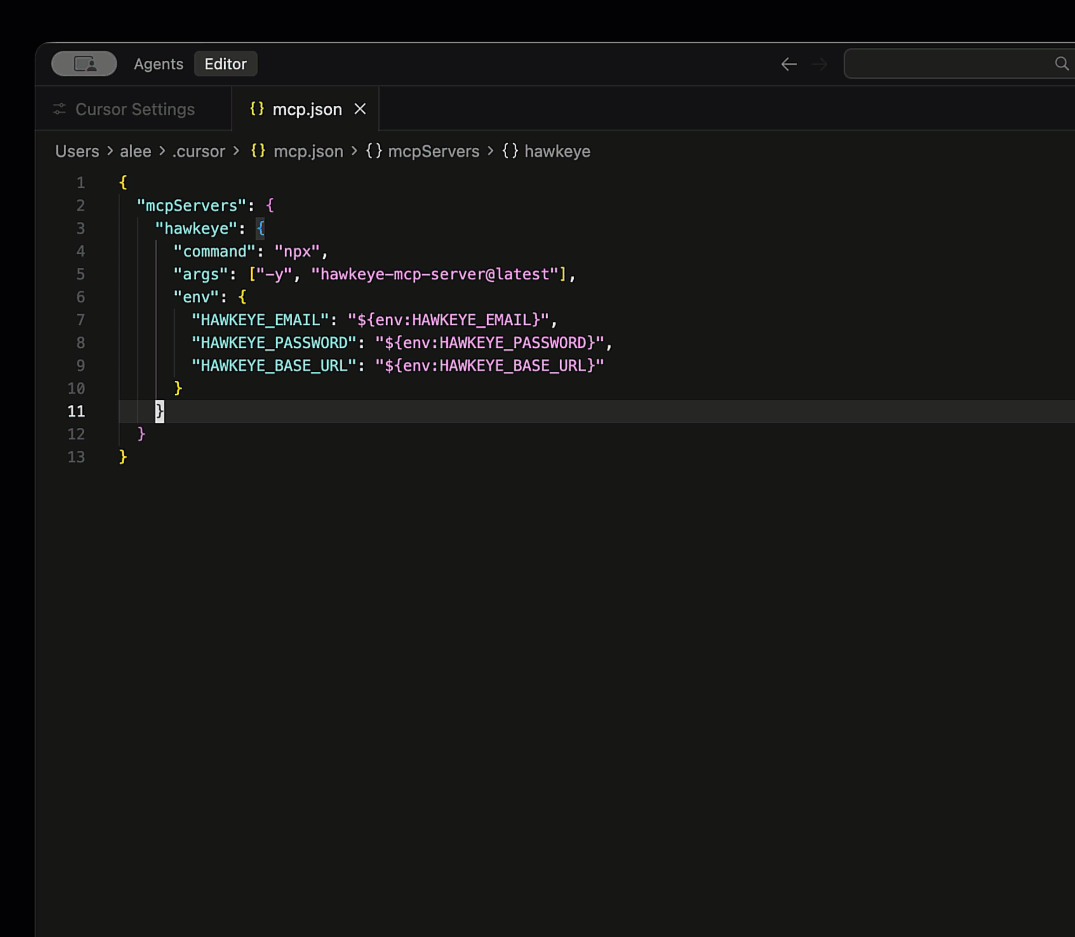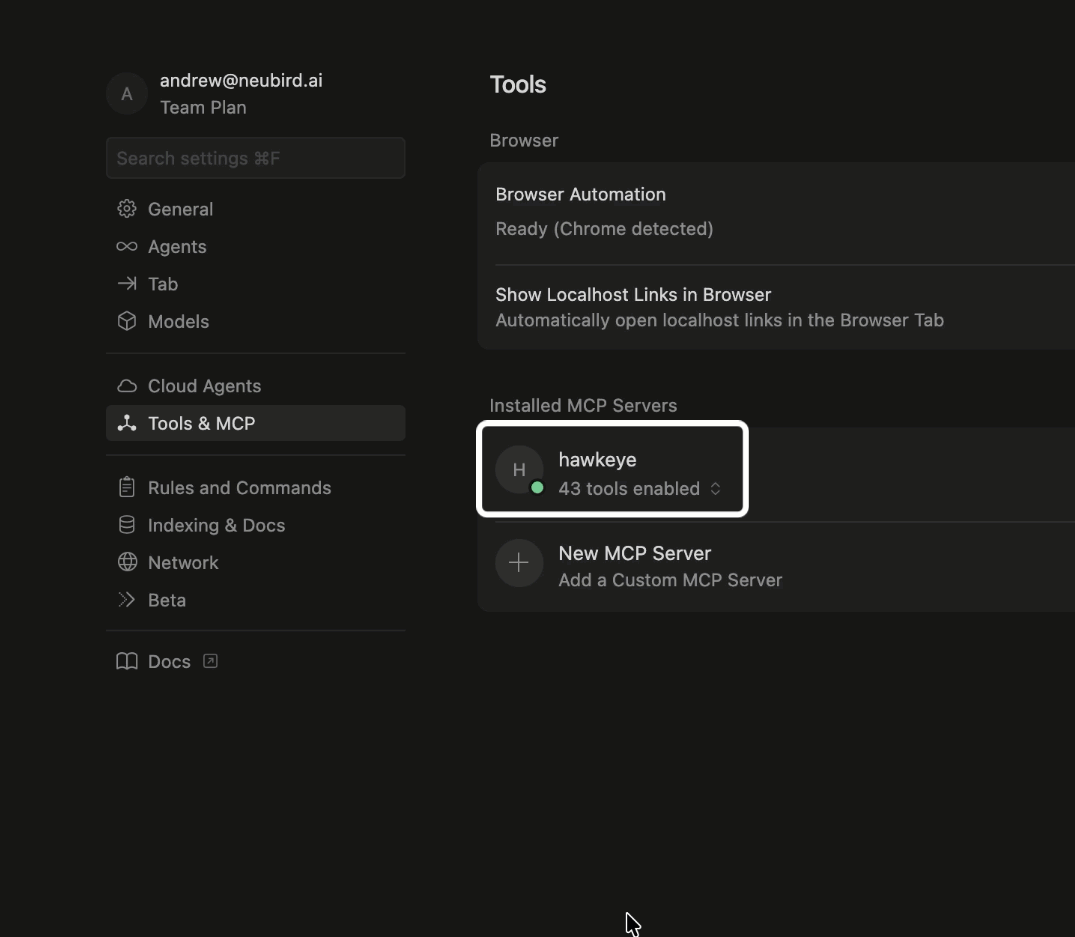
In the Cursor UI, go to Settings > Tools & MCP > Add Custom MCP (or + New MCP Server). Then, paste the following ‘hawkeye’ configuration to run a local MCP server.
{ "mcpServers": { "hawkeye": { "command": "npx", "args": ["-y", "hawkeye-mcp-server@latest"], "env": { "HAWKEYE_EMAIL": "${env:HAWKEYE_EMAIL}", "HAWKEYE_PASSWORD": "${env:HAWKEYE_PASSWORD}", "HAWKEYE_BASE_URL": "${env:HAWKEYE_BASE_URL}" } } } }
Note: Remote MCP server with token-based authentication is coming soon.
In the Cursor MCP configuration under Installed MCP Servers, you should see a green circle with the number of tools listed for Hawkeye, which indicates a successful connection.
Investigate and Remediate Alerts
The following queries are examples of how you can interact with Hawkeye using MCP to retrieve alerts from connected sources, run an investigation, and fix issues using Hawkeye’s RCA and remediation steps.
- List any uninvestigated alerts in Hawkeye and identify which one to address first
This prompt retrieves alerts from the chosen project in Hawkeye and references the metadata of the alerts to order them from highest to lowest priority.
- Run an investigation on the critical alert and retrieve the RCA
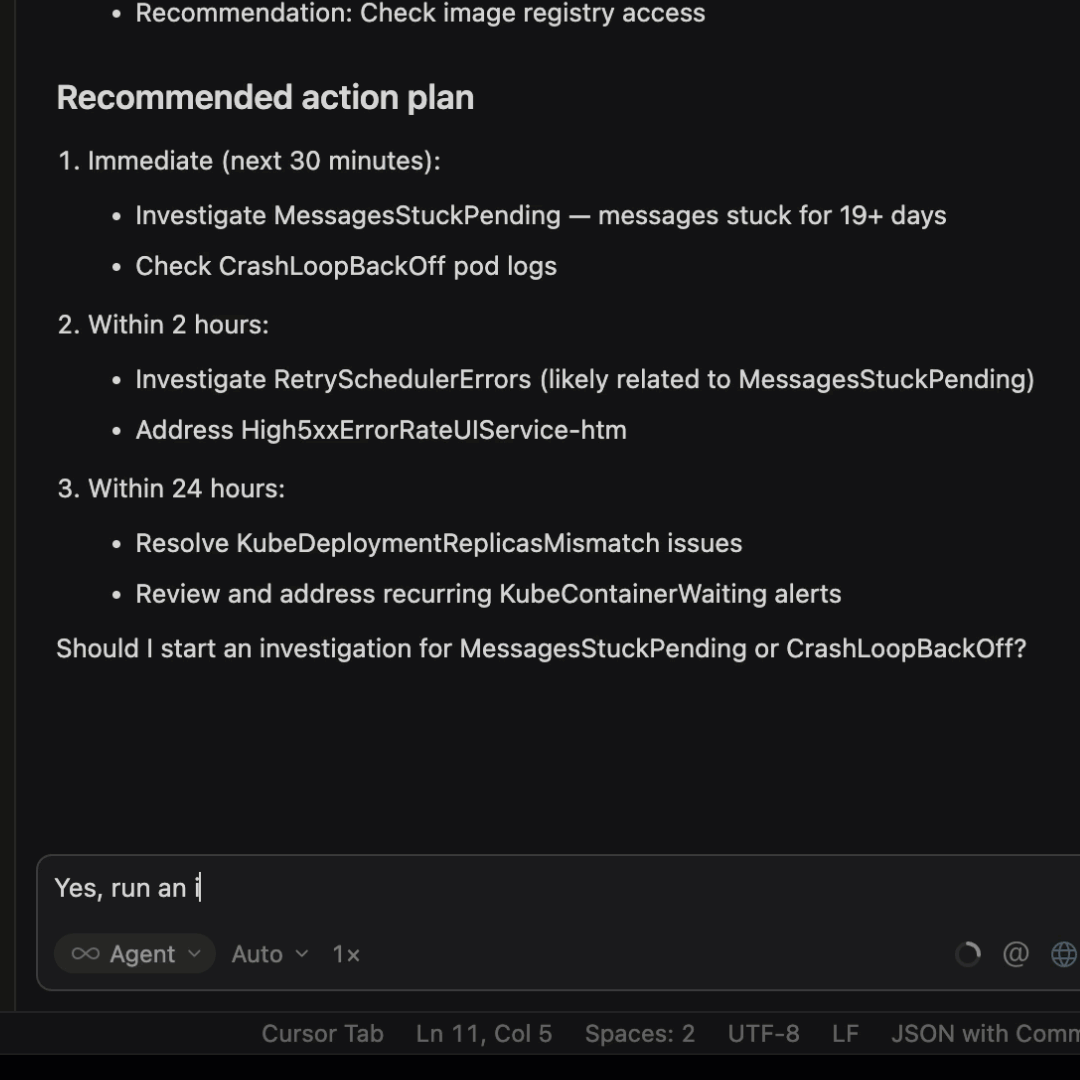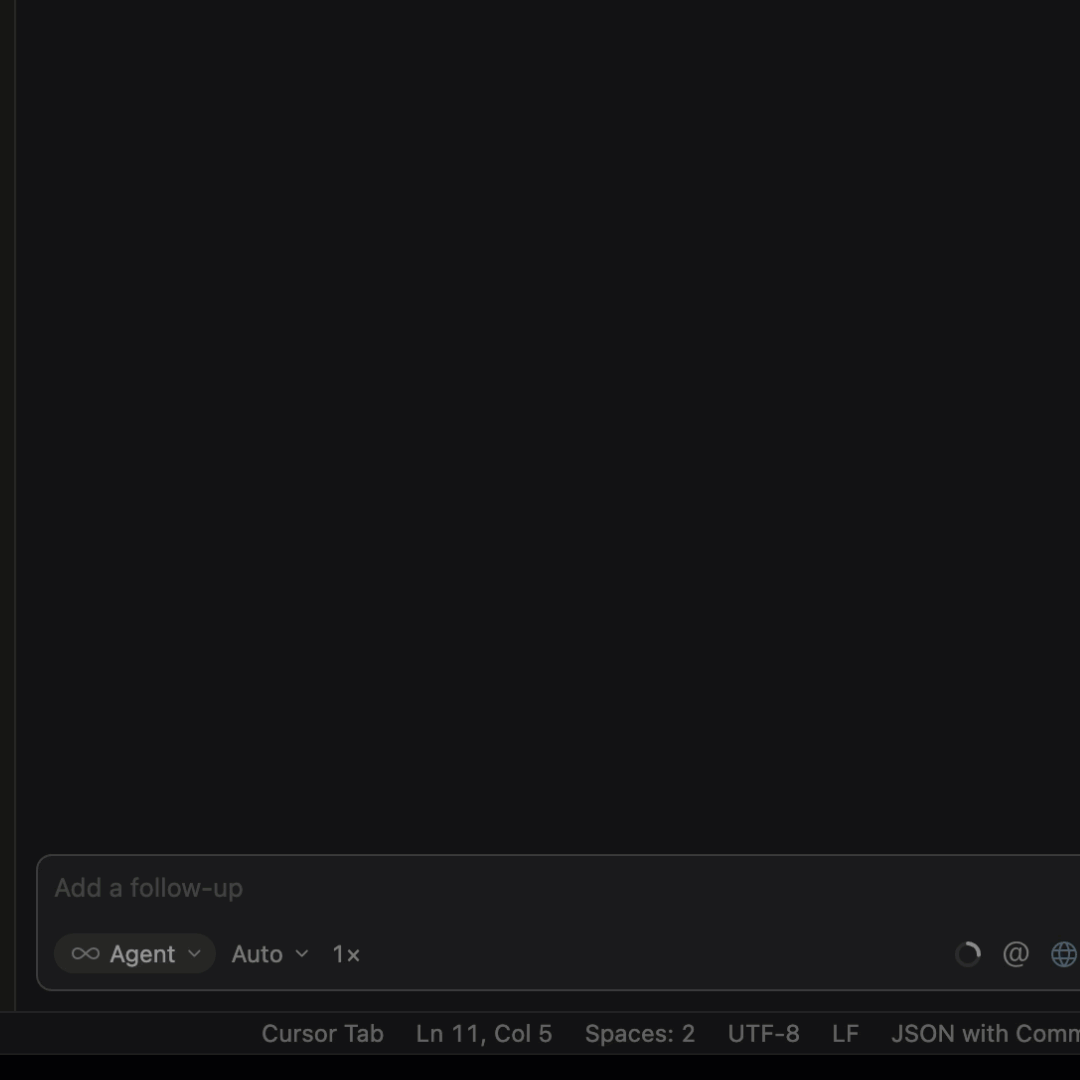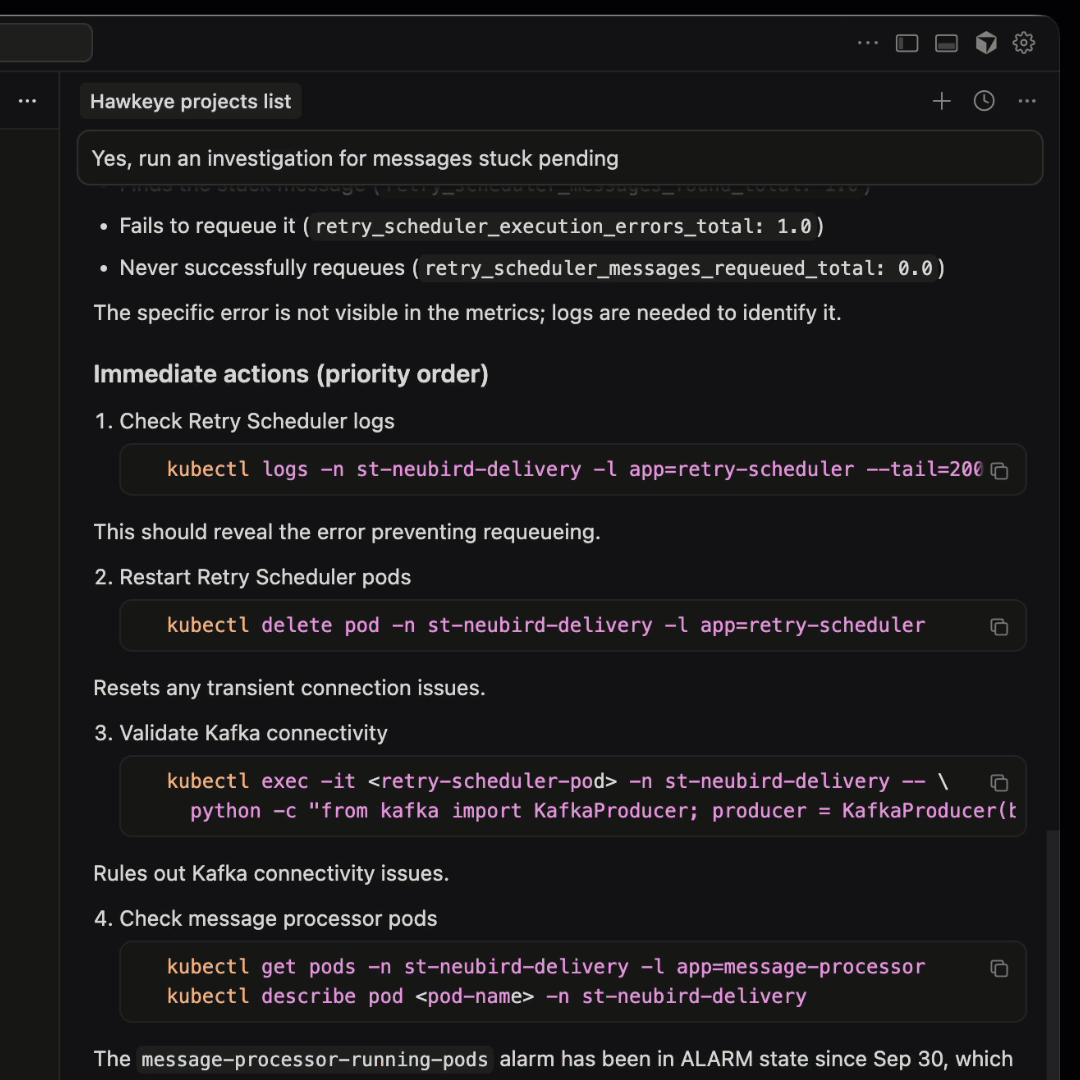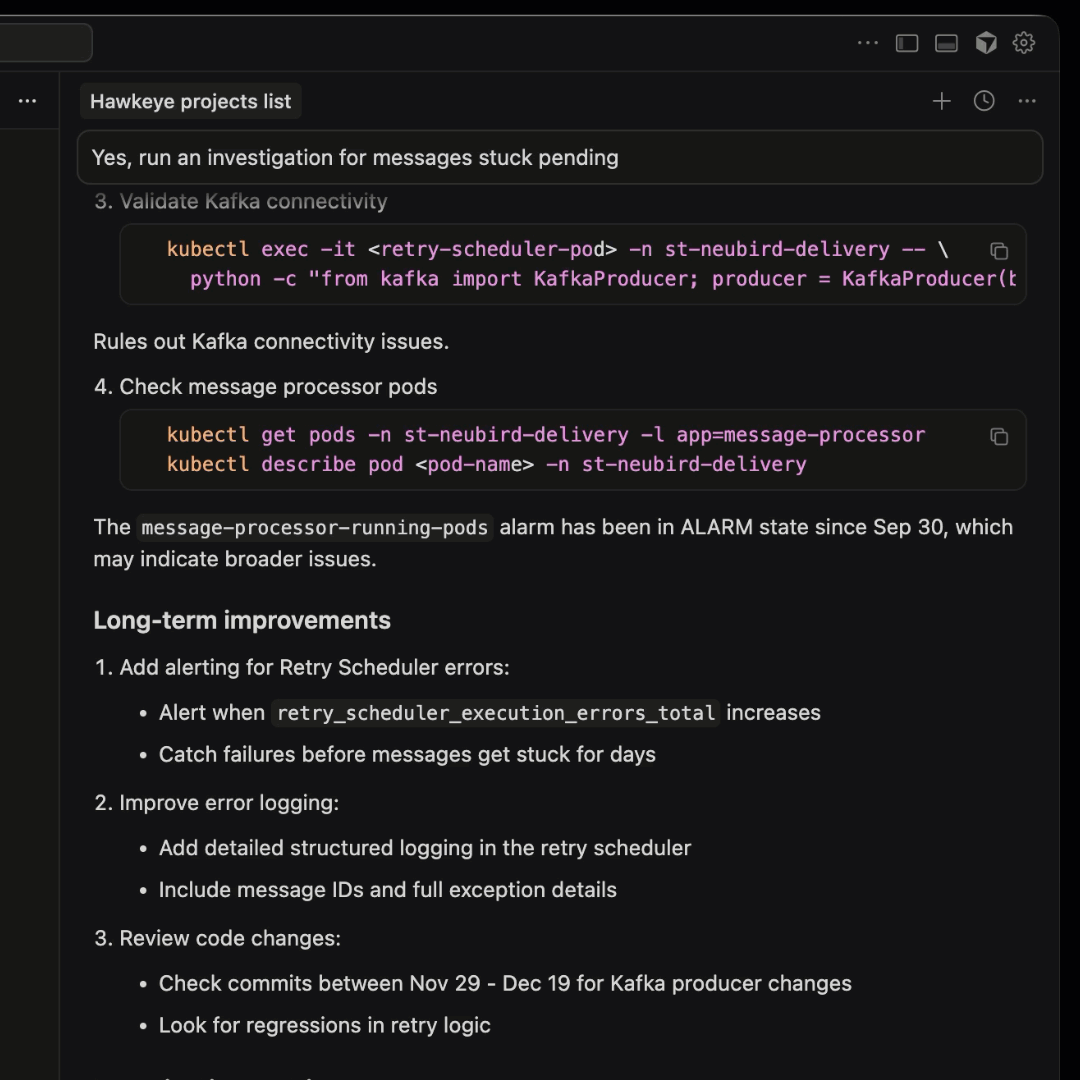
This prompt runs an investigation on Hawkeye, which produces the RCA. The remediation steps and recommendations are now loaded into Cursor’s context.
- Refer to the remediation steps from Hawkeye and create a Pull Request (PR) in GitHub with suggested changes
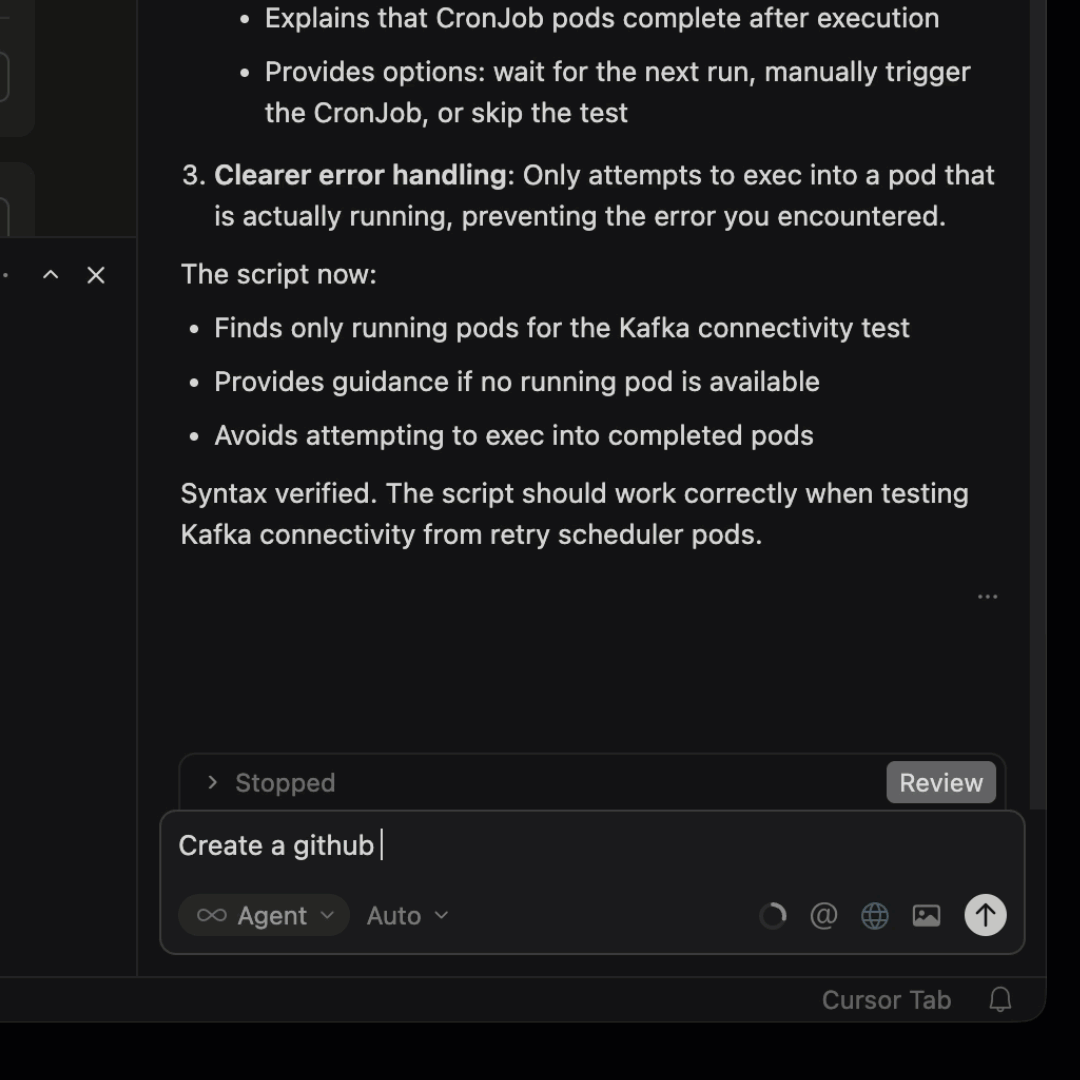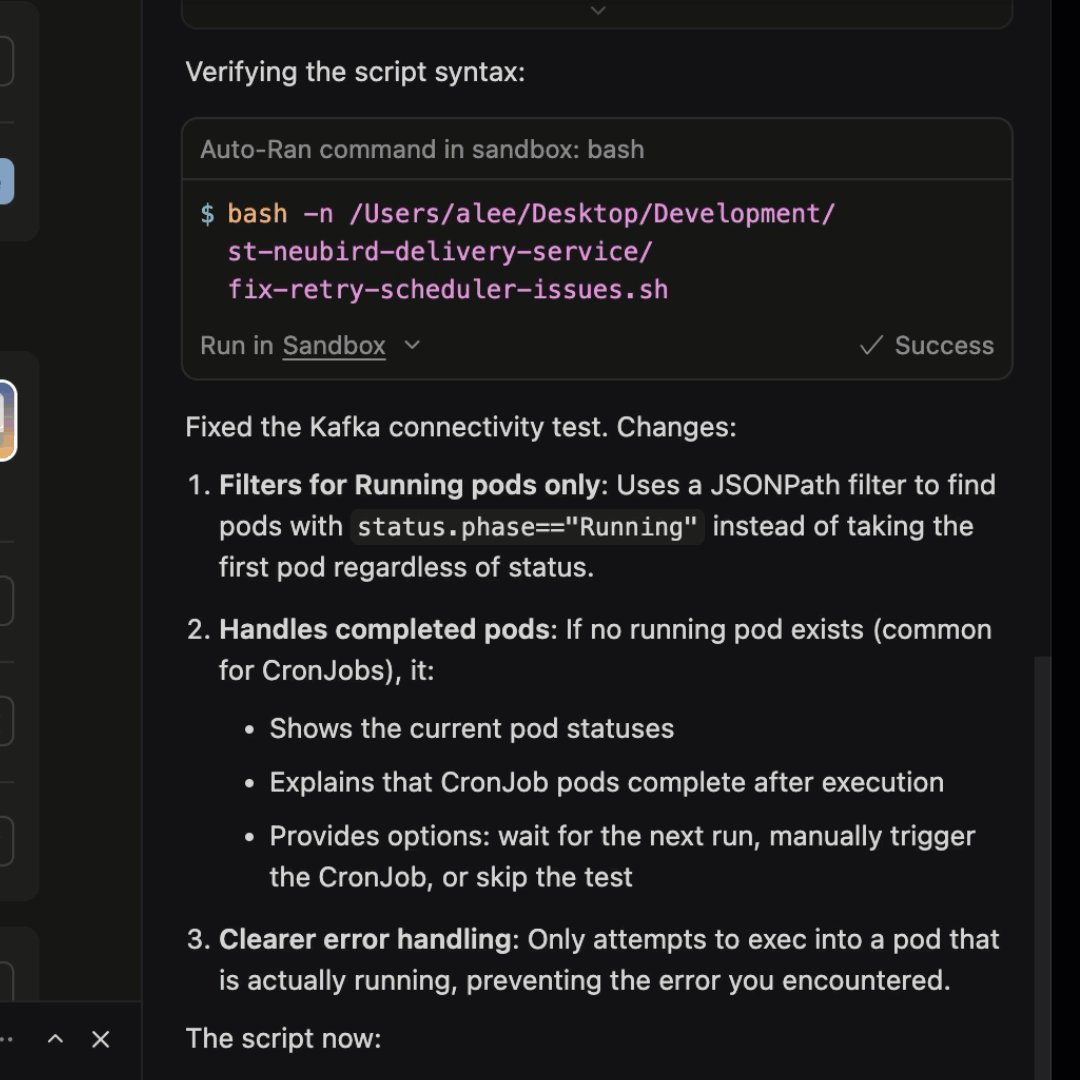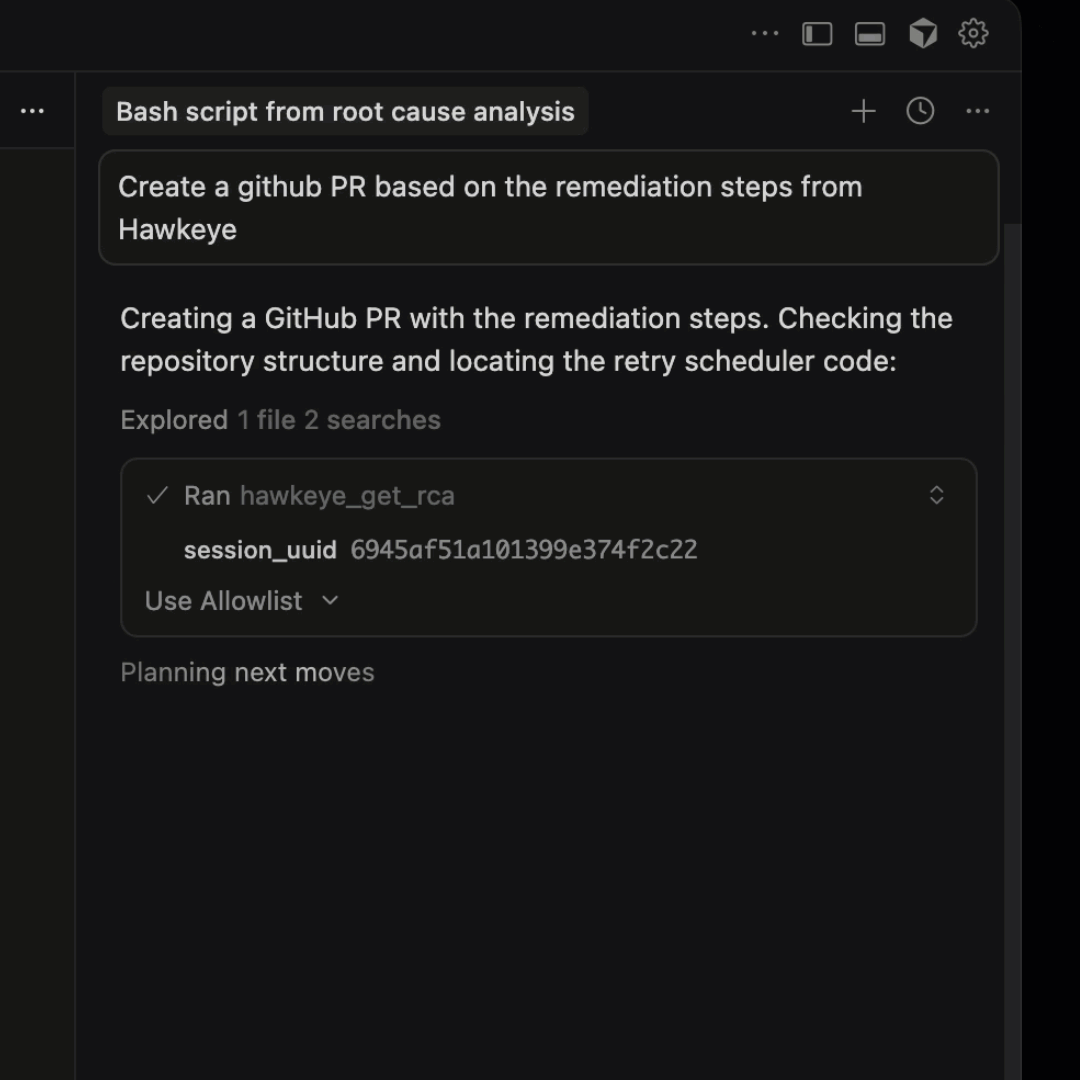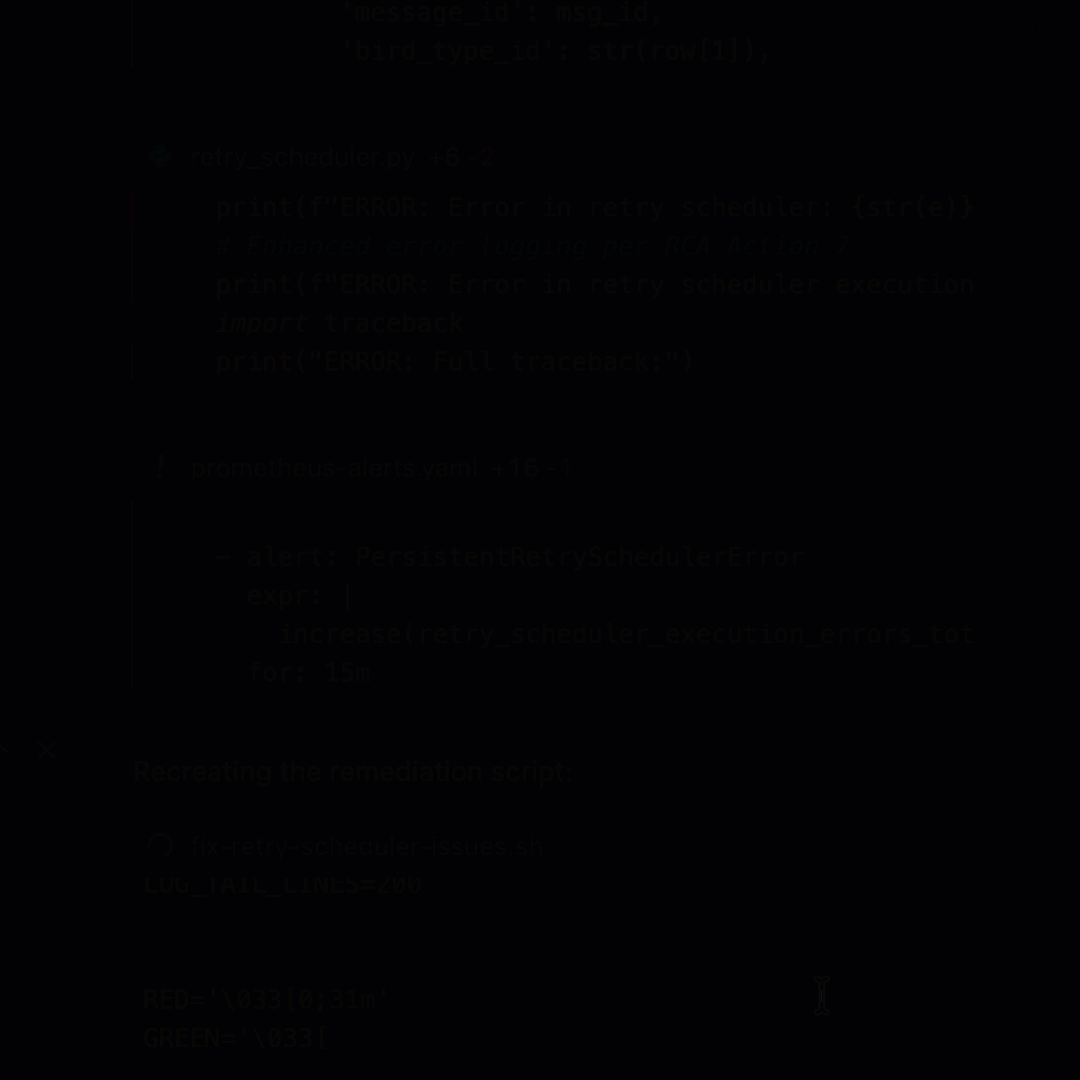
Cursor uses LLMs to generate a code change based on the RCA provided by Hawkeye.
With just these three prompts, I am able to get a detailed root cause analysis, remediation steps to fix the issue, improved alerting mechanism to catch more details, and a first commit towards a PR.
Next Steps
Now that you have access to our AI SRE Agent’s powerful context engineering across multiple environments, you can leverage it to automatically investigate issues such as:
- What changed in the last 30 minutes across all environments that correlates with this latency spike?
- Correlate this customer-reported issue with backend traces, logs, and infrastructure metrics for their request.
- What’s the blast radius if this node/zone/region fails right now?
Once Hawkeye investigates the issue, you will get detailed remediation steps and recommendations that can be referenced by the LLM to create code and config changes. This brings you closer than ever to a fully automated lifecycle of incident creation to incident resolution, right in your development environment.
Written by